Simple reverse engineering - postage
The binary, script for exploitation, and a PDF of the solution can be found in this repository:
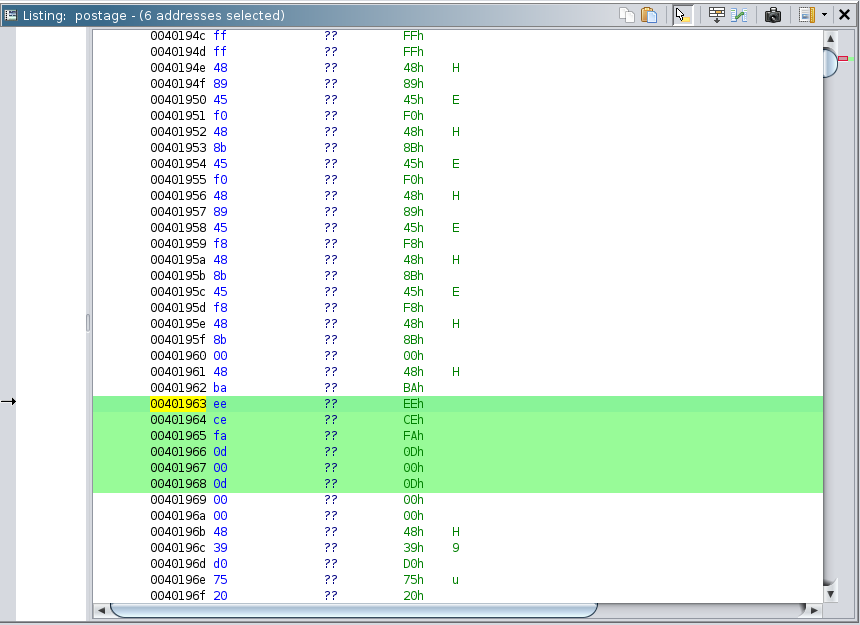
Binary, script for exploitation, and PDF of solutionI completed this challenge by using checksec and analyzing the disassembly output. It can be noted with checksec that PIE is off.
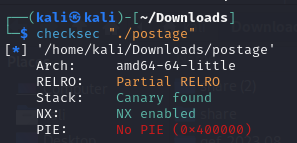
This means that the program runs using the same location in virtual memory every time. This is relevant because this program gives the student the flag if they can give them a number such that if it is turned into a pointer and dereferenced, the program will get back 0xd000dfaceee. So, I found the part of the memory that stores 0xd000dfaceee (401963) and converted that hex address to decimal to get the answer (4200803). Since the program runs using the same virtual addresses every time, this number should work for every run.